-
Content Count
930 -
Donations
$0.00 -
Joined
-
Last visited
-
Days Won
78
Posts posted by freak
-
-
-
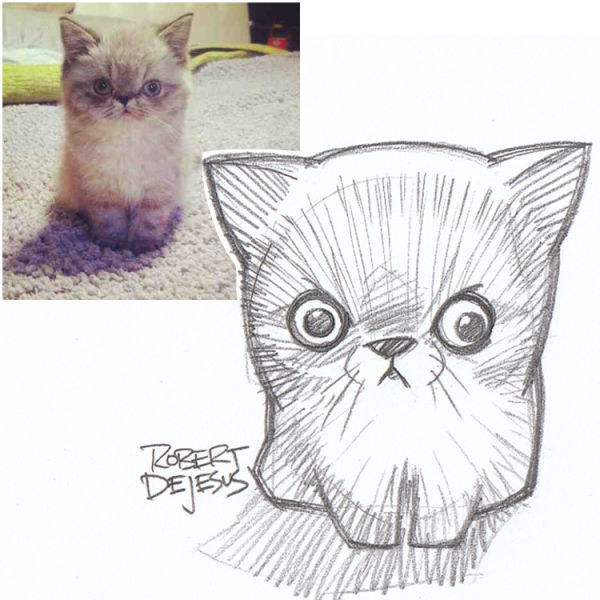
Wang Yu and Li Lintao started building a Lamborghini Diablo four years ago in a garage. They have spent $228,000 on the project and it is an impressive copy of the original sports car. The pair hope to launch their own brand of car in the future.




























-
 1
1
-
-
This Chinese man had a nice sashimi meal but he did not expect this to happen afterwards…
He went to the doctor with stomach ache and itchy skin and scans of his body revealed that it was riddled with tapeworm due to the large amount of raw fish he had eaten. Doctors believe that the sashimi contained tapeworms’ eggs and these parasites can cause cysticercosis, which is an infection that can be life threatening if it reaches the brain.




-
 1
1
-
-
-
-
Clever makeup turns this pretty girl into Walter White in an instant.





-
 1
1
-
-
-
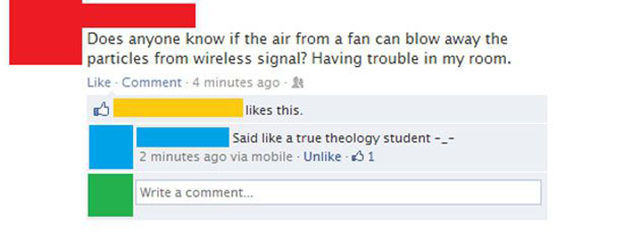
How Attackers Could Crack Your Wireless Network Security
 [/url]
[/url]It’s important to secure your wireless network with WPA2 encryption and a strong passphrase. But what sorts of attacks are you actually securing it against? Here’s how attackers crack encrypted wireless networks.
This isn’t a “how to crack a wireless network” guide. We’re not here to walk you through the process of compromising a network — we want you to understand how someone might compromise your network.
Spying on an Unencrypted Network
First, let’s start with the least secure network possible: An open network with no encryption. Anyone can obviously connect to the network and use your Internet connection without providing a passphrase. This could put you in legal danger if they do something illegal and it’s traced back to your IP address. However, there’s another risk that’s less obvious.
When a network is unencrypted, traffic travels back and forth in plaintext. Anyone within range can use packet-capturing software that activates a laptop’s Wi-Fi hardware and captures the wireless packets from the air. This is generally known as putting the device in “promiscuous mode,” as it captures all nearby wireless traffic. The attacker could then inspect these packets and see what you’re doing online. Any HTTPS connections will be protected from this, but all HTTP traffic will be vulnerable.
Google took some heat for this when they were capturing Wi-Fi data with their Street View trucks. They captured some packets from open Wi-Fi networks, and those could contain sensitive data. Anyone within range of your network can capture this sensitive data — yet another reason to not operate an open Wi-Fi network.

Finding a Hidden Wireless Network
It’s possible to find “hidden” wireless networks with tools like Kismet, which show nearby wireless networks. The wireless network’s SSID, or name, will be displayed as blank in many of these tools.
This won’t help too much. Attackers can send a deauth frame to a device, which is the signal an access point would send if it were shutting down. The device will then attempt to connect to the network again, and it will do so using the network’s SSID. The SSID can be captured at this time. This tool isn’t even really necessary, as monitoring a network for an extended period of time will naturally result in the capture of a client attempting to connect, revealing the SSID.
This is why hiding your wireless network won’t help you. In fact, it can actually make your devices less secure because they’ll attempt to connect to the hidden Wi-Fi network at all times. An attacker nearby could see these requests and pretend to be your hidden access point, forcing your device to connect to a compromised access point.

Changing a MAC Address
Network analysis tools that capture network traffic will also show devices connected to an access point along with their MAC address, something that’s visible in the packets traveling back and forth. If a device is connected to the access point, the attacker knows that the device’s MAC address will work with the device.
The attacker can then change their Wi-Fi hardware’s MAC address to match the other computer’s MAC address. They’d wait for the client to disconnect or deauth it and force it to disconnect, then connect to the Wi-Fi network with their own device.

Cracking WEP or WPA1 Encryption
WPA2 is the modern, secure way to encrypt your Wi-Fi. There are known attacks that can break the older WEP or WPA1 encryption (WPA1 is often referred to just as “WPA” encryption, but we use WPA1 here to emphasize that we’re talking about the older version of WPA and that WPA2 is more secure).
The encryption scheme itself is vulnerable and, with enough traffic captured, the encryption can be analyzed and broken. After monitoring an access point for about a day and capturing about a day’s worth of traffic, an attacker can run a software program that breaks the WEP encryption. WEP is fairly insecure and there are other ways to break it more quickly by tricking the access point. WPA1 is more secure, but is still vulnerable.

Exploiting WPS Vulnerabilities
An attacker could also break into your network by exploiting Wi-Fi Protected Setup, or WPS. With WPS, your router has an 8-digit PIN number that a device can use to connect rather than providing your encryption passphrase. The PIN is checked in two groups — first, the router checks the first four digits and tells the device if they’re right, and then the router checks the last four digits and tells the device if they’re right. There are a fairly small number of possible four-digit numbers, so an attacker can “brute force” the WPS security by trying each four-digit number until the router tells them they’ve guessed the correct one.
You can protect against this by disabling WPS. Unfortunately, some routers actually leave WPS enabled even when you disable it in their web interface. You may be safer if you have a router that doesn’t support WPS at all!

Brute-Forcing WPA2 Passphrases
Modern WPA2 encryption has to be “brute-forced” with a dictionary attack. An attacker monitors a network, capturing the handshake packets that are exchanged when a device connects to an access point. This data can be easily captured by deauthorizing a connected device. They can then attempt to run a brute-force attack, checking possible Wi-Fi passphrases and seeing if they will successfully complete the handshake.
For example, let’s say the passphrase is “password.” WPA2 passphrases must be between eight and 63 digits, so “password” is perfectly valid. A computer would start with a dictionary file containing many possible passphrases and try them one by one. For example, it would try “password,” “letmein,1″ “opensesame,” and so on. This sort of attack is often called a “dictionary attack” because it requires a dictionary file containing many possible passwords.
We can easily see how common or simple passwords like “password” will be guessed within a short time frame, whereas the computer may never get around to guessing a longer, less obvious passphrase like “:]C/+[[ujA+S;n9BYq9
z>T@J#5E=g}uwF5?B?Xyg.” This is why it’s important to have a strong passphrase with a reasonable length. Tools of the Trade
If you want to see the specific tools an attacker would use, download and run Kali Linux. Kali is the successor to BackTrack, which you may have heard about. Aircrack-ng, Kismet, Wireshark, Reaver, and other network-penetration tools are all preinstalled and ready to use. These tools may take some knowledge (or Googling) to actually use, of course.

All these methods require an attacker to be within physical range of the network, of course. If you live in the middle of nowhere, you’re less at risk. If you live in an apartment building in New York City, there are quite a few people nearby who might want an insecure network they can piggy-back on.
-
 3
3
-
-
-
-
Chrismark Castle is on the market for $45 million and with eight bedrooms and 75 acres of land that sits on its very own lake, it is a dream home for anyone who can afford it.
In total, Chrismark Castle has 20 rooms, 12 fireplaces, a maids’ room, library, pool, and massage rooms.
-
 2
2
-
-
-
-
-
The events that occurred on 11 September 2001 will forever be remembered by the world. Here are some heart-breaking photos from the day.
This family photo was taken at the top of the World Trade Center on 10 September 2001 and is one of the last “happy” images taken of the building before devastation struck the following day.
-
 1
1
-
-
-
-
-
Nipple stimulation = a closer bond with your sexual partner.
Or at least that’s what a 2012 study suggests! The study aimed to find exactly why men are attracted to breasts, and the answer they found is that it’s a partial result of evolution. In that men have learned that by stimulating a woman’s nipple, the woman is then more inclined to feel attracted and connected to her partner physically.
In fact, some women can achieve orgasm from nipple stimulation alone. (Awesome.)
In a 2009 study, 29% of the 213 women studied had achieved orgasm from nipple stimulation alone. That’s because women’s brains process genital and nipple stimulation in the same exact way.
There’s a champagne glass in London that’s shaped after Kate Moss’ breast.
The glasses exist at London’s 34 restaurant, and Kate’s signature is even on the bottom!
Men have nipples and breasts because all fetuses are female at first.
That’s right! Every fetus starts as female, and it isn’t until six weeks that testosterone starts to take hold. But even before that six-week mark, nipples and breasts are already part of the body.
The largest bra size is an L, and the smallest is a AAA.
The L cup was only made available in 2011.
Scientists seriously do not know why women have full breasts all the time.
Primates have full breasts only when they’re breastfeeding, and then they quickly go back to normal. But human breasts appear full even when we’re not breastfeeding. So…what gives? There are a bunch of theories, including one about how our full breasts are similar to the round and bright red buttcheeks of our ape ancestors.
Because bras weren’t yet invented, ancient Roman women would wrap bandages around themselves to keep their boobs in place while they worked out.
Studies show that breastfeeding can have long-term benefits for moms, including lowering risks of heart disease and cancer.
Along with helping new moms lose that baby weight, and lowering the chances of postpartum depression.
And breastfeeding actually changes the way a mother’s brain works! It makes the mother more attuned to her own child’s crying.
That’s some Mother Nature witchcraft right there.
Corsets that cinched in the waist and popped up the breasts went out of style during World War I, when the army needed more steel and asked women to give them up.
There are more than 4 million new bras produced every day.
A 2013 study found that men who prefer large breasts are less financially secure.
The study also found that when men are hungry they prefer large breasts, and if they want children they also prefer them large.
And the same study found that men who prefer small breasts are more financially secure.
The small-breast enthusiasts are also less likely to want children.
Sleeping facedown can change the shape of your breasts over time.
It would take a few years of sleeping facedown, but it would change the shape! The best sleep move? On your side.
There are eight different types of nipples.
Variety: It is fun! And for nipples, the varieties include normal, flat, puffy, and inverted!
And just in case you were wondering (obvi), Annie Hawkins-Turner has the world’s largest natural breasts on record.
They measure 70 inches around, 43 inches under, and would technically be supported in a 48V bra, if they made that size.
-
 2
2
-
-
-
Add day of week to taskbar clock in Windows 8 | 7
In this post we will see how to add the day of the week, that is, Monday, Tuesday, etc to the system tray clock in the Taskbar Notification area in Windows 8 or Windows 7.
Add day of week to taskbar
Press Win+X in Windows 8 to bring up the WinX Menu. From it, choose ‘Control Panel’ and then, select Region.
Now, from the ‘Region’ window that appears on your computer screen, select ‘Additional Settings’ button.
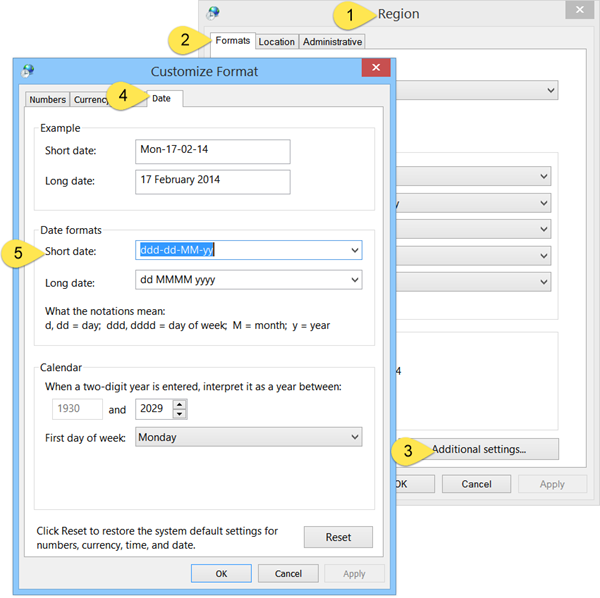
Next, from the ‘Customize Format’ window, choose the ‘Date’ tab.
Under Short date add ddd in the beginning. That is, make the Short date as ddd-dd-MM-yy. In this case only 3 alphabets will be displayed. viz. Mon. If you prefer the full day displayed viz Monday, then use dddd-dd-MM-yy. Using a comma instead of the hyphen, will make a comma display. Try and see if ddd, dd-MM-yy suits you. Put the day after the date by using dd-MM-yy, ddd if you wish.
Play around and see what suits you the best. Click Apply / OK and exit.
You will now see the day of the week to displayed in the taskbar.
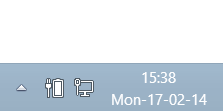
As always, Thank You for your time and I hope you found this How To of interest
-
 1
1
-
-
Poddy Training
Baby is poddy training and not too happy about it and his farting proves it. He wants a magazine and a fuzzy mat for his feet, even a TV to pass the time. Then the poor kid runs out of toilet paper. After all, it's his potty and he'll cry if he wants to--you would cry too if they did this to you.https://www.youtube.com/watch?v=t4FtuXVAM2A
-
 1
1
-
-
Baby Queen: We're Out of Pampers!
These four kids, known as Baby Queen, sing "We're Out of Pampers" to the tune of "We Are the Champions." There's no time for pooing for baby Freddy Mercury because the diaper drawer is empty! When nature calls, you've got to observe. But when the drawer with diapers is empty, and you got to poo, what do you do?
-


















































































































































































































































Lady Gaga Forgets Her Bra at Home on a Night Out in Belgium
in The Fun & Laughs Section
Posted · Report reply