-
Content Count
519 -
Donations
$0.00 -
Joined
-
Last visited
-
Days Won
18
Posts posted by CyberAbc
-
-
u may use phpmyadmin in gui mode to track ur error ......
-
 1
1
-
-
type "services.msc" in command promt and in right tab u will find the adobe services and then disable the service.
-
 1
1
-
-
gr8 post bro
 :yourock:
:yourock: 

-
bro just use the DAZ windows loaded v2.1.4, it will do more than enough to make ur copy genuine without any hassle. i hav already tested.u will hav ur copy genuine and make update the os .Don't worry..........
-
 1
1
-
-
welcome to Dragon_Skull, u r amazing

Happy father's day!!
-
gr8 gr8 gr8................




-
 2
2
-
-
As vigneshnallamad said killdisk is good tools for erase ur disk fully when u want to sell/gift/dispose of hdd and not want to trace any data from ur disk.i will suggest to go for gpated as it is the tools which will format ur partition of any kind partition be it mac/linux/windows.
here is ur link
http://sourceforge.net/projects/gparted/files/gparted-live-stable/0.12.1-5/gparted-live-0.12.1-5.iso
-
 2
2
-
-
probably ur keyboard is short or some key is still pressed down. I hav the problem , if u hav warranty of ur lap they will change the keyboard
-
bro here is the link
http://bitshare.com/files/c10s5k1j/Quickbooks-Pro-2012---eXpLoIt-crack.zip.html
-
possible to wear both?
-
gr8 sense of humor
-
bro look this site for ur ans
http://www.soft.tahionic.com/download-words_extractor/index.html
-
gr8 news i will try...........
-
bro go through this first plz
http://en.wikipedia.org/wiki/Application_programming_interface
-
gr8 site...............

-
Cookie Basics
In April of 2000 I read an in-depth article on Internet privacy in a large, respected newspaper, and that article contained a definition of cookies. Paraphrasing, the definition went like this:
Quote
Cookies are programs that Web sites put on your hard disk. They sit on your computer gathering information about you and everything you do on the Internet, and whenever the Web site wants to it can download all of the information the cookie has collected. [wrong]
Definitions like that are fairly common in the press. The problem is, none of that information is correct. Cookies are not programs, and they cannot run like programs do. Therefore, they cannot gather any information on their own. Nor can they collect any personal information about you from your machine.
Here is a valid definition of a cookie: A cookie is a piece of text that a Web server can store on a user's hard disk. Cookies allow a Web site to store information on a user's machine and later retrieve it. The pieces of information are stored as name-value pairs.
For example, a Web site might generate a unique ID number for each visitor and store the ID number on each user's machine using a cookie file.
*
*Internet Explorer and other browsers store cookies on your computer.
* If you use Microsoft's Internet Explorer to browse the Web, you can see all of the cookies that are stored on your machine. The most common place for them to reside is in a directory called c:windowscookies. When I look in that directory on my machine, I find 165 files. Each file is a text file that contains name-value pairs, and there is one file for each Web site that has placed cookies on my machine.
You can see in the directory that each of these files is a simple, normal text file. You can see which Web site placed the file on your machine by looking at the file name (the information is also stored inside the file). You can open each file by clicking on it.
For example, I have visited goto.com, and the site has placed a cookie on my machine. The cookie file for goto.com contains the following information:
UserID A9A3BECE0563982D www.goto.com/Goto.com has stored on my machine a single name-value pair. The name of the pair is UserID, and the value is A9A3BECE0563982D. The first time I visited goto.com, the site assigned me a unique ID value and stored it on my machine.
(Note that there probably are several other values stored in the file after the three shown above. That is housekeeping information for the browser.)
Amazon.com stores a bit more information on my machine. When I look at the cookie file Amazon has created on my machine, it contains the following:
session-id-time 954242000 amazon.com/ session-id 002-4135256-7625846 amazon.com/ x-main eKQIfwnxuF7qtmX52x6VWAXh@Ih6Uo5H amazon.com/ ubid-main 077-9263437-9645324 amazon.com/It appears that Amazon stores a main user ID, an ID for each session, and the time the session started on my machine (as well as an x-main value, which could be anything).
The vast majority of sites store just one piece of information -- a user ID -- on your machine. But a site can store many name-value pairs if it wants to.
A name-value pair is simply a named piece of data. It is not a program, and it cannot "do" anything. A Web site can retrieve only the information that it has placed on your machine. It cannot retrieve information from other cookie files, nor any other information from your machine.
How does cookie data move?
As you saw in the previous section, cookie data is simply name-value pairs stored on your hard disk by a Web site. That is all cookie data is. The Web site stores the data, and later it receives it back. A Web site can only receive the data it has stored on your machine. It cannot look at any other cookie, nor anything else on your machine.
When you type a URL into a web browser, a web server might look in your cookie file.
The data moves in the following manner:
•If you type the URL of a Web site into your browser, your browser sends a request to the Web site for the page (see How Web Servers Work for a discussion). For example, if you type the URL http://www.amazon.com into your browser, your browser will contact Amazon's server and request its home page.
•When the browser does this, it will look on your machine for a cookie file that Amazon has set. If it finds an Amazon cookie file, your browser will send all of the name-value pairs in the file to Amazon's server along with the URL. If it finds no cookie file, it will send no cookie data.
•Amazon's Web server receives the cookie data and the request for a page. If name-value pairs are received, Amazon can use them.
•If no name-value pairs are received, Amazon knows that you have not visited before. The server creates a new ID for you in Amazon's database and then sends name-value pairs to your machine in the header for the Web page it sends. Your machine stores the name-value pairs on your hard disk.
•The Web server can change name-value pairs or add new pairs whenever you visit the site and request a page.
There are other pieces of information that the server can send with the name-value pair. One of these is an expiration date. Another is a path (so that the site can associate different cookie values with different parts of the site).
You have control over this process. You can set an option in your browser so that the browser informs you every time a site sends name-value pairs to you. You can then accept or deny the values.
How do Web sites use cookies?
Cookies evolved because they solve a big problem for the people who implement Web sites. In the broadest sense, a cookie allows a site to store state information on your machine. This information lets a Web site remember what state your browser is in. An ID is one simple piece of state information -- if an ID exists on your machine, the site knows that you have visited before. The state is, "Your browser has visited the site at least one time," and the site knows your ID from that visit.
Web sites use cookies in many different ways. Here are some of the most common examples:
•Sites can accurately determine how many people actually visit the site. It turns out that because of proxy servers, caching, concentrators and so on, the only way for a site to accurately count visitors is to set a cookie with a unique ID for each visitor. Using cookies, sites can determine:
•How many visitors arrive
•How many are new versus repeat visitors
•How often a visitor has visited
The way the site does this is by using a database. The first time a visitor arrives, the site creates a new ID in the database and sends the ID as a cookie. The next time the user comes back, the site can increment a counter associated with that ID in the database and know how many times that visitor returns.
•Sites can store user preferences so that the site can look different for each visitor (often referred to as customization). For example, if you visit msn.com, it offers you the ability to "change content/layout/color." It also allows you to enter your zip code and get customized weather information. When you enter your zip code, the following name-value pair gets added to MSN's cookie file:
WEAT CC=NC%5FRaleigh%2DDurham®ION= www.msn.com/Since I live in Raleigh, N.C., this makes sense.
Most sites seem to store preferences like this in the site's database and store nothing but an ID as a cookie, but storing the actual values in name-value pairs is another way to do it (we'll discuss later why this approach has lost favor).
•E-commerce sites can implement things like shopping carts and "quick checkout" options. The cookie contains an ID and lets the site keep track of you as you add different things to your cart. Each item you add to your shopping cart is stored in the site's database along with your ID value. When you check out, the site knows what is in your cart by retrieving all of your selections from the database. It would be impossible to implement a convenient shopping mechanism without cookies or something like them.
* In all of these examples, note that what the database is able to store is things you have selected from the site, pages you have viewed from the site, information you have given to the site in online forms, etc. All of the information is stored in the site's database, and in most cases, a cookie containing your unique ID is all that is stored on your computer.
Problems with Cookies
Cookies are not a perfect state mechanism, but they certainly make a lot of things possible that would be impossible otherwise. Here are several of the things that make cookies imperfect.
•People often share machines - Any machine that is used in a public area, and many machines used in an office environment or at home, are shared by multiple people. Let's say that you use a public machine (in a library, for example) to purchase something from an online store. The store will leave a cookie on the machine, and someone could later try to purchase something from the store using your account. Stores usually post large warnings about this problem, and that is why. Even so, mistakes can happen. For example, I had once used my wife's machine to purchase something from Amazon. Later, she visited Amazon and clicked the "one-click" button, not realizing that it really does allow the purchase of a book in exactly one click.
On something like a Windows NT machine or a UNIX machine that uses accounts properly, this is not a problem. The accounts separate all of the users' cookies. Accounts are much more relaxed in other operating systems, and it is a problem.
If you try the example above on a public machine, and if other people using the machine have visited HowStuffWorks, then the history URL may show a very long list of files.
•Cookies get erased - If you have a problem with your browser and call tech support, probably the first thing that tech support will ask you to do is to erase all of the temporary Internet files on your machine. When you do that, you lose all of your cookie files. Now when you visit a site again, that site will think you are a new user and assign you a new cookie. This tends to skew the site's record of new versus return visitors, and it also can make it hard for you to recover previously stored preferences. This is why sites ask you to register in some cases -- if you register with a user name and a password, you can log in, even if you lose your cookie file, and restore your preferences. If preference values are stored directly on the machine (as in the MSN weather example above), then recovery is impossible. That is why many sites now store all user information in a central database and store only an ID value on the user's machine.
If you erase your cookie file for HowStuffWorks and then revisit the history URL in the previous section, you will find that HowStuffWorks has no history for you. The site has to create a new ID and cookie file for you, and that new ID has no data stored against it in the database. (Also note that the HowStuffWorks Registration System allows you to reset your history list whenever you like.)
•Multiple machines - People often use more than one machine during the day. For example, I have a machine in the office, a machine at home and a laptop for the road. Unless the site is specifically engineered to solve the problem, I will have three unique cookie files on all three machines. Any site that I visit from all three machines will track me as three separate users. It can be annoying to set preferences three times. Again, a site that allows registration and stores preferences centrally may make it easy for me to have the same account on three machines, but the site developers must plan for this when designing the site.
If you visit the history URL demonstrated in the previous section from one machine and then try it again from another, you will find that your history lists are different. This is because the server created two IDs for you, one on each machine.
There are probably not any easy solutions to these problems, except asking users to register and storing everything in a central database.
When you register with the HowStuffWorks registration system, the problem is solved in the following way: The site remembers your cookie value and stores it with your registration information. If you take the time to log in from any other machine (or a machine that has lost its cookie files), then the server will modify the cookie file on that machine to contain the ID associated with your registration information. You can therefore have multiple machines with the same ID value.
Cookies on the Internet: Privacy Issues
If you have read the article to this point, you may be wondering why there has been such an uproar in the media about cookies and Internet privacy. You have seen in this article that cookies are benign text files, and you have also seen that they provide lots of useful capabilities on the Web.
There are two things that have caused the strong reaction around cookies:
•The first is something that has plagued consumers for decades. Let's say that you purchase something from a traditional mail order catalog. The catalog company has your name, address and phone number from your order, and it also knows what items you have purchased. It can sell your information to others who might want to sell similar products to you. That is the fuel that makes telemarketing and junk mail possible.
On a Web site, the site can track not only your purchases, but also the pages that you read, the ads that you click on, etc. If you then purchase something and enter your name and address, the site potentially knows much more about you than a traditional mail order company does. This makes targeting much more precise, and that makes a lot of people uncomfortable.
Different sites have different policies. HowStuffWorks has a strict privacy policy and does not sell or share any personal information about our readers with any third party except in cases where you specifically tell us to do so (for example, in an opt-in e-mail program). We do aggregate information together and distribute it. For example, if a reporter asks me how many visitors HowStuffWorks has or which page on the site is the most popular, we create those aggregate statistics from data in the database.
•The second is unique to the Internet. There are certain infrastructure providers that can actually create cookies that are visible on multiple sites. DoubleClick is the most famous example of this. Many companies use DoubleClick to serve banner ads on their sites. DoubleClick can place small (1x1 pixels) GIF files on the site that allow DoubleClick to load cookies on your machine. DoubleClick can then track your movements across multiple sites. It can potentially see the search strings that you type into search engines (due more to the way some search engines implement their systems, not because anything sinister is intended). Because it can gather so much information about you from multiple sites, DoubleClick can form very rich profiles. These are still anonymous, but they are rich.
DoubleClick then went one step further. By acquiring a company, DoubleClick threatened to link these rich anonymous profiles back to name and address information -- it threatened to personalize them, and then sell the data. That began to look very much like spying to most people, and that is what caused the uproar.
DoubleClick and companies like it are in a unique position to do this sort of thing, because they serve ads on so many sites. Cross-site profiling is not a capability available to individual sites, because cookies are site specific.
Cookie in a nutshell
A message given to a Web browser by a Web server. The browser stores the message in a text file. The message is then sent back to the server each time the browser requests a page from the server.
The main purpose of cookies is to identify users and possibly prepare customized Web pages for them. When you enter a Web site using cookies, you may be asked to fill out a form providing such information as your name and interests. This information is packaged into a cookie and sent to your Web browser which stores it for later use. The next time you go to the same Web site, your browser will send the cookie to the Web server. The server can use this information to present you with custom Web pages. So, for example, instead of seeing just a generic welcome page you might see a welcome page with your name on it.
The name cookie derives from UNIX objects called magic cookies. These are tokens that are attached to a user or program and change depending on the areas entered by the user or program.
Cookie by Question and Answer
This infomation is compiled from all over the web.
What is a Cookie?
A cookie is a text-only string that gets entered into the memory of your browser. This value of a variable that a website sets. If the lifetime of this value is set to be longer than the time you spend at that site, then this string is saved to file for future reference.
What are the purposes of cookies?
Cookies make the interaction between users and web sites faster and easier. Without cookies, it would be very difficult for a web site to allow a visitor to fill up a shopping cart or to remember the user's preferences or registration details for a future visit. Web sites use cookies mainly because they save time and make the browsing experience more efficient and enjoyable. Web sites often use cookies for the purposes of collecting demographic information about their users. Cookies enable web sites to monitor their users' web surfing habits and profile them for marketing purposes (for example, to find out which products or services they are interested in and send them targeted advertisements).
Are cookies dangerous?
In a nutshell the answer is no. Cookies are small pieces of text. They are not computer programs, and they can't be executed as code. Also, they cannot be used to disseminate viruses, and versions of Internet Browsers such as IE, Firefox etc.. allow users to set their own limitations to the number of cookies saved on their hard drives. However, as i said in the previous paragraph, some cookies do track internet browsing and provide a certain level of infomation that the user may not warm to. The truth is that revealing any kind of personal information opens the door for that information to be spread, but we are talking about primitive internet usage and not your bank details.
How do Browsers handle Cookies?
•Most browsers offer the following cookie choices:
•Accept all cookies
•Accept only cookies that get sent back to originating server
•Disable all cookies
•Warn me before accepting a cookie.
-
 3
3
-
-
Method 1
1.Using cd rom
2.boot from pendrive(using usb)
1.Using cd rom
by Trinity Rescue Kit 3.4:
http://trinityhome.org/Home/index.php?content=TRINITY_RESCUE_KIT_DOWNLOAD&front_id=12&lang=en&locale=en
from there u download the iso and burn into cd using nero or any burner u like
a.now boot from cd using cd u burned
b. this will look like this
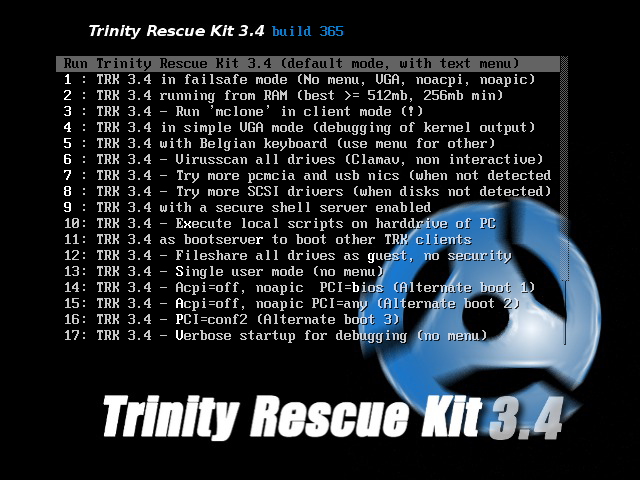
c. now u got ultimately this screen
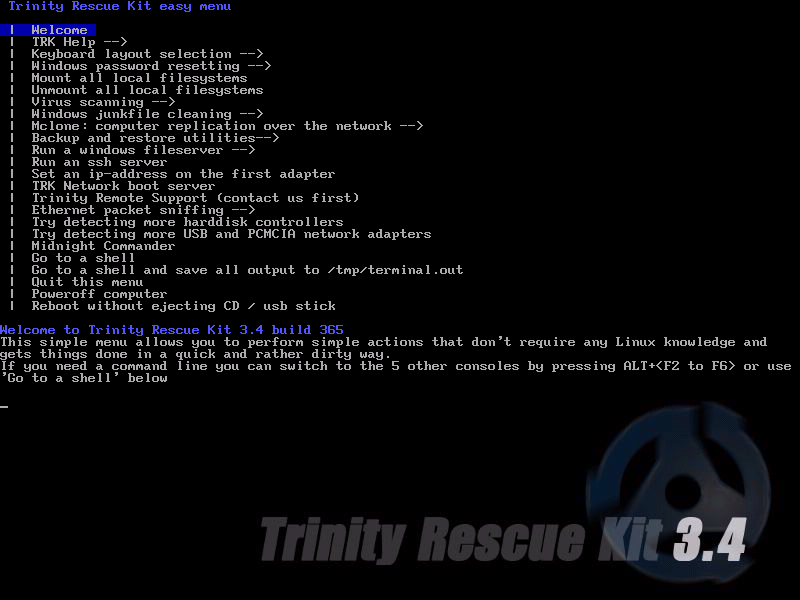
d. now goto "windows password resetting" menu
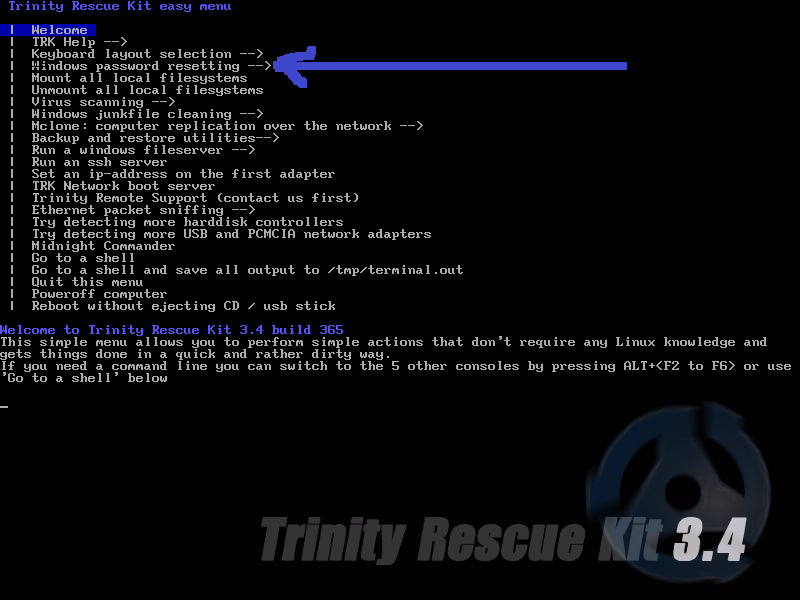
e.now u get this menu
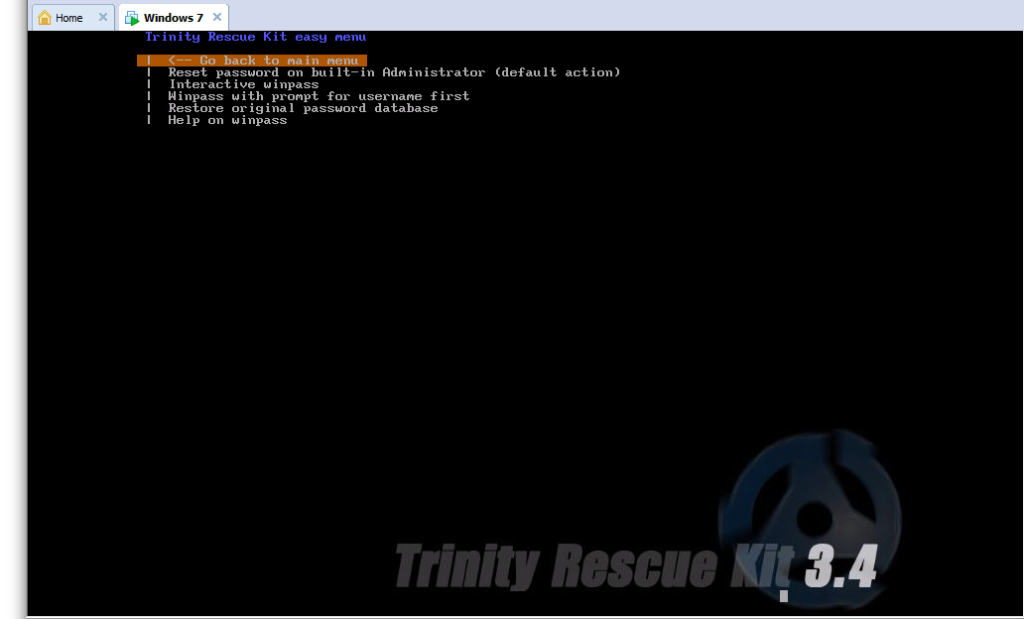
f. if u r administrator then go for option 1(default action)
g. and if if u r user of admin group or any group goto this menu
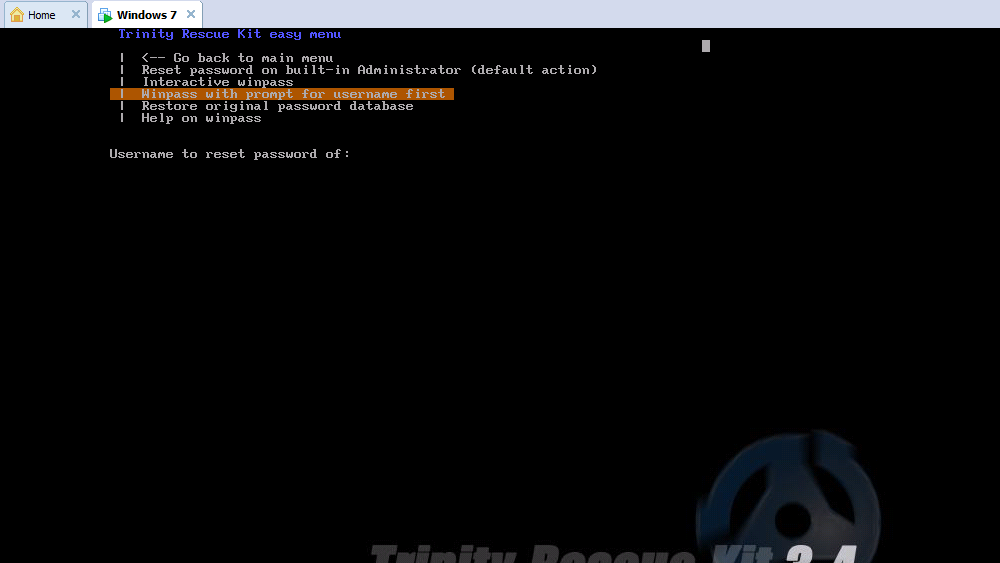
then if if u enter ur user name then go for option one for resetting blank password
2.boot from pendrive(using usb)
a. first goto pendrivelinux and download
http://www.pendrivelinux.com/downloads/YUMI/YUMI-0.0.6.1.exe
this will look like this

b. from here goto system tools and then goto trinity rescue option then add the iso u downloaded from option 1
c. after booting from pendrive the menu will look as follows:

d.from system tools u find the trinity option
e. this will same as from 1.Using cd rom option b.
enjoy!
cyberwarez33
"Sharing is Caring"
Note: if u hav any query plz reply here
-
 6
6
-
-
here is the solution i found..........
STOP 0x0000008E Error Messages
The STOP 0x0000008E error will always appear on a STOP message, more commonly called a Blue Screen of Death (BSOD). One of the errors below or a combination of both errors may display on the STOP message:
"STOP: 0x0000008E"
"KERNEL_MODE_EXCEPTION_NOT_HANDLED"
The STOP 0x0000008E error may also be abbreviated as STOP 0x8E but the full STOP code will always be what's displayed on the blue screen STOP message.
If Windows is able to start after the STOP 0x8E error, you may be prompted with a Windows has recovered from an unexpected shutdown message that shows:
Problem Event Name: BlueScreen
BCCode: 8e
Cause of STOP 0x0000008E Errors
STOP 0x0000008E errors are usually caused by memory hardware failures and more rarely by device driver issues, viruses, or hardware failures other than your RAM.
If STOP 0x0000008E isn't the exact STOP code you're seeing or KERNEL_MODE_EXCEPTION_NOT_HANDLED isn't the exact message, please check my Complete List of STOP Error Codes and reference the troubleshooting information for the STOP message that you are seeing.
How To Fix STOP 0x0000008E Errors
1. Restart your computer if you haven't already done so. The STOP 0x0000008E blue screen error might be a fluke.
2. Did you just install new hardware or make a change to some hardware or a hardware driver? If so, there's a very good chance that the change you made caused the STOP 0x0000008E error.
Undo the change you made and test for the 0x8E blue screen error.
Depending on what change you made, some solutions might include:
- Remove or reconfigure the newly installed hardware.
- Startup with Last Known Good Configuration to undo related registry and driver changes.
- Use System Restore to undo recent changes.
- Roll back any device drivers you've installed to versions prior to your update.
- Test your RAM. The most common cause of the STOP 0x0000008E error is memory that is damaged or has stopped working properly for some reason.
- Replace any nonworking memory modules if your tests show a problem.
3. Verify that the system memory is properly installed. Memory that's installed in some way other than that suggested by your motherboard manufacturer could cause STOP 0x0000008E errors and other related problems.
Note: If you have any doubt about the proper memory configuration in your computer, please consult your computer or motherboard manual. All motherboards have fairly stringent requirements on the types and configurations of RAM modules.
4.Return BIOS settings to their default levels. Overclocked or misconfigured memory settings in BIOS have been known to cause STOP 0x0000008E errors.
Note: If you've made several customizations to your BIOS settings and don't want to load the default ones then at least try returning all BIOS memory timing, caching, and shadowing options to their default levels and see if that fixes the STOP 0x0000008E error.
5.Apply all available Windows updates. Several service packs and other patches have specifically addressed STOP 0x0000008E issues.
Note: This particular solution is likely to solve your problem if your STOP 0x0000008E error is accompanied by a mention of win32k.sys or wdmaud.sys, or if it occurred while making changes to the hardware acceleration on your graphics card.
6. If STOP error 0x0000008E is followed by 0xc0000005, as in STOP: 0x0000008E (0xc0000005, x, x, x), applying the latest Windows service pack will likely fix your issue.
7. Perform basic STOP error troubleshooting. If none of the specific steps above help fix the STOP 0x0000008E error you're seeing, take a look at this general STOP error troubleshooting guide. Since most STOP errors are similarly caused, some of the suggestions might help.
Please let me know if you've fixed a blue screen of death with the STOP 0x0000008E STOP code using a method that I don't have above. I'd like to keep this page updated with the most accurate STOP 0x0000008E error troubleshooting information as possible.
Applies To
Any of Microsoft's Windows NT based operating systems could experience the STOP 0x0000008E error. This includes Windows 7, Windows Vista, Windows XP, Windows 2000, and Windows NT.
-
 1
1
- Remove or reconfigure the newly installed hardware.
-
do what dirtylow said. i think u installed the os without formatting the c:\ .
to access "program file" you need to take ownership of the folder they are in. Make sure simplefile sharing is turned off then log in as an administrator and go to your old profile folder (C:\documents and settings\username) and right click it. Choose properties from the drop down menu - select the security tab - add your new username and give full control - click advanced - select owner tab - select your new username and click apply.
-
 1
1
-
-
bro plz clearly explain what u actually want
-
as vigneshnallamad said Windows Security Essentials consume lots of memory that's true and i am adding one point its doing nothing.Kis is the best as i am using it for last 3 years.
-
1. Open notepad
2.Then copy and paste the code below
3.This will looks like below
4.save the file anything .bat namely menu.bat
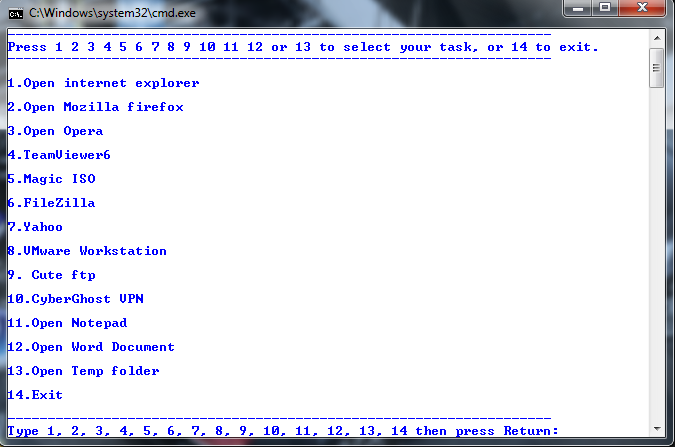
@echo off cls color f9 :menu echo. echo -------------------------------------------------------------------- echo Press 1 2 3 4 5 6 7 8 9 10 11 12 or 13 to select your task, or 14 to exit. echo -------------------------------------------------------------------- echo. echo 1.Open internet explorer echo. echo 2.Open Mozilla firefox echo. echo 3.Open Opera echo. echo 4.TeamViewer6 echo. echo 5.Magic ISO echo. echo 6.FileZilla echo. echo 7.Yahoo echo. echo 8.VMware Workstation echo. echo 9. Typing Instructor Platinum echo. echo 10.CyberGhost VPN echo. echo 11.Open Notepad echo. echo 12.Open Word Document echo. echo 13.Open Temp folder echo. echo 14.Exit echo. echo -------------------------------------------------------------------- set /p m=Type 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14 then press Return: if %m%==1 goto explorer if %m%==2 goto mozilla if %m%==3 goto opera if %m%==4 goto Teamviewer if %m%==5 goto MagicISO if %m%==6 goto FileZilla if %m%==7 goto Yahoo if %m%==8 goto vmware if %m%==9 goto Typing if %m%==10 goto vpn if %m%==11 goto note if %m%==12 goto word if %m%==13 goto temp if %m%==14 goto end :explorer start iexplore.exe goto menu :mozilla start firefox.exe goto menu :opera start "" /b "C:\Program Files (x86)\Opera\opera.exe" %* goto menu :teamviewer start "" /b "C:\Program Files (x86)\TeamViewer\Version7\TeamViewer.exe" %* goto menu :MagicISO start "" /b "C:\Program Files\MagicISO\MagicISO.exe" %* goto menu :FileZilla start "" /b "C:\Program Files\FileZilla FTP Client\filezilla.exe" %* goto menu :Yahoo start "" /b "C:\Program Files\Yahoo!\Messenger\YahooMessenger.exe" %* goto menu :vmware start "" /b "C:\Program Files\VMware\VMware Workstation\vmware.exe" %* goto menu :Typing start "" /b "C:\Program Files\Individual Software\Typing Instructor\Typing Instructor.exe" %* goto menu :vpn start "" /b "C:\Program Files\S.A.D\CyberGhost VPN\CyberGhost.exe" %* goto menu :note start notepad.exe goto menu :word start winword goto menu :temp start %temp% goto menu :end
Note: for win7 64 bit just replace the program menu. As for example "C:\Program Files\Yahoo!\Messenger\YahooMessenger.exe" with "C:\Program Files (x86)\Yahoo!\Messenger\YahooMessenger.exe"
-
i have a gr8 code i used to use it from desktop to access any program quickly instead of going start menu--------->all program----->required program
-
gr8 gr8 news.......
i hav been enlighten by the knoledge.
thank u so much.
-
 1
1
-



Help with php
in Programming (C#, C++, JAVA, VB, .NET, PHPetc.)
Posted · Report reply
bro u can create that table by gui mode by using phpmyadmin on wamp/mamp/lamp server based on what os u r using and then copy the code and use in php.