-
Content Count
50 -
Donations
$0.00 -
Joined
-
Last visited
-
Days Won
9
Posts posted by Cyb3r3vil
-
-
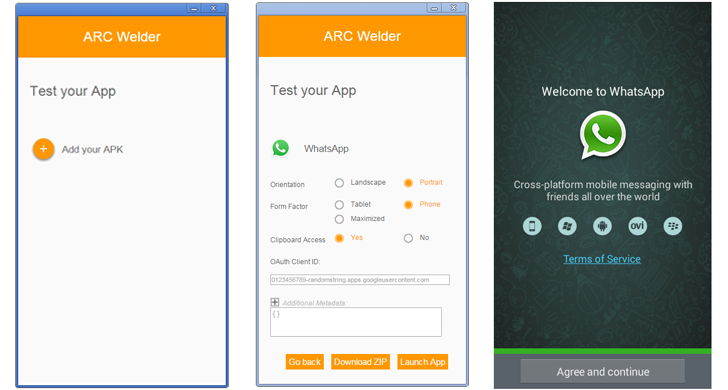
Last year at Google I/O developer event, Google Launched
a limited beta "App Runtime for Chrome" (ARC) project, which now expanded to run millions of Android apps within Chrome browser.Google has released a new developer tool called App Runtime for Chrome (ARC) Welder that allows Android apps to run on Chrome for Linux, Windows, and OS X systems.App Runtime for Chrome (ARC) was an early experiment specifically designed for app developers, but now anyone can download it.Google Chrome's ARC Welder app can now run any of your favorite Android apps like WhatsApp, Candy Crush, Angry Birds, all from your Chrome BrowserARC welder tool operates via some special runtime implemented using Native Client (NaCl) in-browser binary execution tech.Native Client is a Chrome sandboxing technology that allows Chrome plugins and apps to run at near-native speeds, taking full advantage of the system's CPU and GPU.Google ported complete Android stack to Native Client, allowing Android apps to run on most major operating systems.Google ARC welder tool is based on Android 4.4, but there are some limitations:- you can load only one app at a time
- you have to select portrait or landscape layout
- you need to choose, whether you want the app to run on phone- or tablet-style.
- LEARN HOW TO RUN ANDROID APPS IN CHROME:-
- Install the latest Google Chrome Browser Download and run the ARC Welder APP from the Chrome Store.
- Add third party APK file host.
- After downloading APK app file to your PC, click Open.
- Select the mode -> "Tablet" or "Phone" -> in which you want to run your app.
- Finally, click the "Launch App" button.
- I have personally tried this tool before writing, and some of my favorite Android apps work pretty well.
-
https://developer.chrome.com/apps/getstarted_arc
Google for app developers to use ARC and test Android app for use on Chrome OS devices.
-
 1
1
-
fun to play with Thankz ShAmmY1989
-
 1
1
-
-

http://www.songfacts.com
This is what i was wondering about and how i found this cool site
The Call Of Ktulu by Metallica
http://www.songfacts.com/artist-metallica.php
-
Written by James Hetfield, Lars Ulrich, Cliff Burton and original Metallica guitarist Dave Mustaine, this instrumental was inspired by the story The Call Of Cthulhu by H.P. Lovecraft. The author is a big influence on Metallica. His work also inspired their song "Thing That Should Not Be." http://www.songfacts.com/detail.php?id=1869
-
In the book, the story says that mentioning the name Cthulhu (Verbally or written) will bring him closer. That's why Metallica used the name "Ktulu" and not "Cthulhu" - for fear of the beast. (thanks, diego - Panama)
 CP Moderator Message: Mr Grumpy - Coded links
CP Moderator Message: Mr Grumpy - Coded links
-
 1
1
-
-

Last week, at the WinHEC (Windows Hardware Engineering Community) summit in China, Microsoft announced that Windows 10 is expected to officially launch this summer. It also stunned the tech world with news that even pirated versions of Windows will be eligible for the free upgrade to Windows 10. At face value, it may seem like Microsoft is simply caving and giving digital amnesty to millions who are using Windows illegally, but there's most likely a method to the madness.
There are two possible motives for allowing pirated versions of Windows to be upgraded for free. Microsoft appears to be going through a transition in terms of the Windows business model. It's also possible that Microsoft could pull the plug on those pirated versions of Windows 10 at some point in the future.
Hook 'emIt's a tried and true strategy that has worked for centuries. It's a twist on the classic "puppy dog close." Give consumers enough of a taste to get them hooked, and then turn them into paying customers.
Mobile device updates have changed user expectations, and Apple has already paved the way with Mac OS X for making upgrades to the desktop OS free for all users. While Microsoft has been clear that its magnanimous gift of free Windows 10 will expire after one year, I won't be surprised in the least if that policy changes and Windows upgrades remain free in perpetuity.
It remains to be seen whether Microsoft will transition to a Windows-as-a-Service or Windows 365 type model. Even that could be construed as a free version of Windows, where customers are really just paying for additional perks and benefits.
Regardless of how all that plays out, though, the reality is that the world had shifted, and Microsoft has to shift with it. That means finding new ways to monetize services and generate revenue. The bottom line is that Microsoft needs as many customers as possible to be invested in the Windows 10 ecosystem so it has the largest possible pool of potential customers for whatever products and services it chooses to market through the OS.
Shut 'em downThere has also been some speculation that with Windows 10, automatic updates may not be optional for customers. Reading the fine print of what Microsoft described for the free upgrades, it seems like updates might be a condition of using the OS.
Paul Thurrott pointed out a line that states Microsoft will keep the new OS current for the supported lifetime of the device at no additional charge. "This suggests to me that keeping Windows 10 up-to-date going forward is not optional. That in order to get this offer -- or perhaps just to get Windows 10 as a consumer, regardless -- will require you to let Microsoft keep your system up-to-date."
It's possible that Microsoft could offer a free update to Windows 10 as bait to get those running pirated versions of Windows to make the switch. Then it could push out an update that flips a switch to block or disable all Windows systems that don't have a valid activation code. If there's no way to opt out of the updates, there would be no way for those running "pirated" versions of Windows 10 to prevent the update.
The first strategy is much more likely. Microsoft has much more to gain from building the biggest potential market for Windows goods and services than it does from kicking millions of users out of the Windows ecosystem. Maybe it can separate those who are actually buying goods and services from those who are truly freeloading and just shut down those systems that aren't contributing anything to the bottom line anyway.
-
 1
1
-
-
http://showmystreet.com/
kinda LIKE GOOGLE EARTH !
-
 1
1
-
-

Giveaway of the Day Software
I Know most of you already know of this awesome site for the ones that don't
you can download cool software here and it's free stuff and Legitimate !
http://www.giveawayoftheday.com/
-
 2
2
-
-
Cyb3r3vil
cyber-1.a combining form meaning “computer,” “computer network,” or “virtual reality,” used in the formation of compound words ( cybertalk; cyberart; cyberspace) and by extension meaning “very modern” ( cyberfashion).eviladjective1.morally wrong or bad; immoral; wicked:evil deeds; an evil life.2.harmful; injurious:evil laws.3.characterized or accompanied by misfortune or suffering; unfortunate; disastrous:to be fallen on evil days.4.due to actual or imputed bad conduct or character:an evil reputation.5.nounmarked by anger, irritability, irascibility, etc.:He is known for his evil disposition.6.that which is evil; evil quality, intention, or conduct:to choose the lesser of two evils.7.the force in nature that governs and gives rise to wickedness and sin.8.the wicked or immoral part of someone or something:The evil in his nature has destroyed the good.9.harm; mischief; misfortune:to wish one evil.10.anything causing injury or harm:Tobacco is considered by some to be an evil.11.a harmful aspect, effect, or consequence:the evils of alcohol.12.adverba disease, as king's evil.13.Idiomsin an evil manner; badly; ill:It went evil with him.14.the evil one, the devil; Satan.before 900; Middle English evel, evil, Old English yfel; cognate with Gothic ubils, Old High German ubil, German übel, Old Frisian, Middle Dutch evelevil- Every mortal must learn that there is neither power nor reality in evil.
- It is society that interferes with tom, and not personified evil.
- Peck came to the conclusion that possession was a rare phenomenon related to evil.
evil
adj.
Old English yfel (Kentish evel) "bad, vicious, ill, wicked," from Proto-Germanic *ubilaz (cf. Old Saxon ubil, Old Frisian and Middle Dutch evel, Dutch euvel, Old High German ubil, German übel, Gothic ubils), from PIE *upelo-, from root *wap- (cf. Hittite huwapp- "evil").
"In OE., as in all the other early Teut. langs., exc. Scandinavian, this word is the most comprehensive adjectival expression of disapproval, dislike or disparagement" [OED]. Evil was the word the Anglo-Saxons used where we would use bad, cruel, unskillful, defective (adj.), or harm, crime, misfortune, disease (n.). The meaning "extreme moral wickedness" was in Old English, but did not become the main sense until 18c. Related: Evilly. Evil eye (Latin oculus malus) was Old English eage yfel. Evilchild is attested as an English surname from 13c.U.S.AThe Axis of Cyber Evil: A North Korean Case of Cyber EspionageOctober 10, 2013
By: MacDonnell Ulsch

China, Russia, Syria, Iran and North Korea are long established cyber threats that have evolving into a post-Cold War axis of cyber evil that is escalating in intensity and should be taken seriously by any entity, government or private sector, possessing valuable proprietary information. And the stakes are getting higher.
-
 2
2
-
 The joint operation by authorities of the U.S. Federal Bureau of Investigation (FBI) and European law enforcement seized Silk Road 2.0, an alternative to the notorious online illegal-drug marketplace last week, and arrested 26-year-old operator Blake Benthall, but that wasn't the end.US and European authorities over the weekend announced the seizure of 27 different websites as part of a much larger operation called Operation Onymous, which led to take-down of more than "410 hidden services" that sell illegal goods and services from drugs to murder-for-hire assassins by masking their identities using the Tor encryption network."The action aimed to stop the sale, distribution and promotion of illegal and harmful items, including weapons and drugs, which were being sold on online ‘dark’ marketplaces," according to the Europol press release.This globally-coordinated take down is the combined efforts of 17 nations which includes the law enforcement agencies in the U.S. and 16 member nations of Europol. The operation led to the arrest of 17 people, operators of darknet websites and the seizure of $1 million in Bitcoin, 180,000 Euros in cash, drugs, gold and silver.According to U.S. authorities, Operation Onymous is the largest law enforcement action till now against the illegal websites operating on the Tor network, which helps users to communicate anonymously by hiding their IP addresses."We are not 'just' removing these services from the open Internet, said Troels Oerting, Head of Europol's EC3 (European Cybercrime Centre) cyber crime unit. "This time we have also hit services on the Darknet using Tor where, for a long time, criminals have considered themselves beyond reach. We can now show that they are neither invisible nor untouchable. The criminals can run but they can’t hide. And our work continues."The authorities have not yet publicly disclosed the full list of the seized Tor websites, but it appears that less than 20% of the total darknet website have been shut down in the joint cyber crime operation including the seizure of Silk Road 2.0 earlier this week."Silk Road" was the notorious online illegal-drug marketplace that generated $8 million in monthly sales and attracted 150,000 vendors and customers. The FBI seized the darknet website in October of 2013 and after five weeks, Silk Road 2.0 was launched.On Sunday, the Tor Project said it has no idea how the law enforcement authorities were able to identify the servers that were shut down last week as part of Operation Onymous. "We not contacted directly or indirectly by Europol nor any other agency involved," a spokesperson for the Tor project "Phobos" said in a statement.Subscribe Our Newsletter
The joint operation by authorities of the U.S. Federal Bureau of Investigation (FBI) and European law enforcement seized Silk Road 2.0, an alternative to the notorious online illegal-drug marketplace last week, and arrested 26-year-old operator Blake Benthall, but that wasn't the end.US and European authorities over the weekend announced the seizure of 27 different websites as part of a much larger operation called Operation Onymous, which led to take-down of more than "410 hidden services" that sell illegal goods and services from drugs to murder-for-hire assassins by masking their identities using the Tor encryption network."The action aimed to stop the sale, distribution and promotion of illegal and harmful items, including weapons and drugs, which were being sold on online ‘dark’ marketplaces," according to the Europol press release.This globally-coordinated take down is the combined efforts of 17 nations which includes the law enforcement agencies in the U.S. and 16 member nations of Europol. The operation led to the arrest of 17 people, operators of darknet websites and the seizure of $1 million in Bitcoin, 180,000 Euros in cash, drugs, gold and silver.According to U.S. authorities, Operation Onymous is the largest law enforcement action till now against the illegal websites operating on the Tor network, which helps users to communicate anonymously by hiding their IP addresses."We are not 'just' removing these services from the open Internet, said Troels Oerting, Head of Europol's EC3 (European Cybercrime Centre) cyber crime unit. "This time we have also hit services on the Darknet using Tor where, for a long time, criminals have considered themselves beyond reach. We can now show that they are neither invisible nor untouchable. The criminals can run but they can’t hide. And our work continues."The authorities have not yet publicly disclosed the full list of the seized Tor websites, but it appears that less than 20% of the total darknet website have been shut down in the joint cyber crime operation including the seizure of Silk Road 2.0 earlier this week."Silk Road" was the notorious online illegal-drug marketplace that generated $8 million in monthly sales and attracted 150,000 vendors and customers. The FBI seized the darknet website in October of 2013 and after five weeks, Silk Road 2.0 was launched.On Sunday, the Tor Project said it has no idea how the law enforcement authorities were able to identify the servers that were shut down last week as part of Operation Onymous. "We not contacted directly or indirectly by Europol nor any other agency involved," a spokesperson for the Tor project "Phobos" said in a statement.Subscribe Our Newsletter -
 The FBI officers have arrested a 20-year-old Tennessee man and charged with federal computer hacking for allegedly conspiring to launch cyber attacks on five organizations in 2013, including two universities and three companies in the US and Canada, federal law enforcement officials announced today.The accused named Timothy Justin French, who go online by the name “Orbit,” is a key member of the collective “NullCrew” hacking group, that claimed responsibility for dozens of high-profile computer attacks against corporations, educational institutions, and government agencies.NullCrew is a hacktivist group that came into light in 2012 after a successful cyber attack against the World Health Organization (WHO) and Public Broadcasting Service (PBS) in 2012, which resulted in plain-text username and passwords being posted online on Pastebin.The group, represent itself as a part of Anonymous hacking collective, has since 2012 carried out a number of similar high profile cyber attacks, including a successful infiltration into the servers run by the U.S. Department of Homeland Security last year.The accused was arrested without incident by FBI agents at his home in Morristown, Tenn., east of Knoxville, last week and is about to face prosecution in U.S. District Court in Chicago.French, who allegedly used the online handles such as “Orbit,” “@Orbit,” “@Orbit_g1rl,” “crysis,” “rootcrysis,” and “c0rps3,” was charged with conspiracy to commit computer fraud and abuse.The FBI has been working with a "confidential witness" to engage members of the NullCrew hacking group in a chat conversation on Skype, Twitter, and Cryptocat. Unknowingly, during the chat conversations, the NullCrew members discussed past, present, and future hacking attacks and shared current computer vulnerabilities used in the attacks.With the help of these information, the Federal officers tracked the IP address of one of the computers used in those five attacks as well as during other online attacks, which later found to be at French's address in Tennessee. All the records found from the victims’ computers show access from the same IP address at or around the time the attacks."Cyber crime sometimes involves new-age technology but age-old criminal activity ― unlawful intrusion, theft of confidential information, and financial harm to victims," said Zachary Fardon, who has appointed up-and-coming young Assistant U.S. Attorney for the Northern District of Illinois as a deputy section chief in charge of targeting Internet crime, in a statement."Hackers who think they can anonymously steal private business and personal information from computer systems should be aware that we are determined to find them, to prosecute pernicious online activity, and to protect cyber victims," Fardon added.If convicted, French faces a maximum sentence of 10 years in prison and a $250,000 fine.
The FBI officers have arrested a 20-year-old Tennessee man and charged with federal computer hacking for allegedly conspiring to launch cyber attacks on five organizations in 2013, including two universities and three companies in the US and Canada, federal law enforcement officials announced today.The accused named Timothy Justin French, who go online by the name “Orbit,” is a key member of the collective “NullCrew” hacking group, that claimed responsibility for dozens of high-profile computer attacks against corporations, educational institutions, and government agencies.NullCrew is a hacktivist group that came into light in 2012 after a successful cyber attack against the World Health Organization (WHO) and Public Broadcasting Service (PBS) in 2012, which resulted in plain-text username and passwords being posted online on Pastebin.The group, represent itself as a part of Anonymous hacking collective, has since 2012 carried out a number of similar high profile cyber attacks, including a successful infiltration into the servers run by the U.S. Department of Homeland Security last year.The accused was arrested without incident by FBI agents at his home in Morristown, Tenn., east of Knoxville, last week and is about to face prosecution in U.S. District Court in Chicago.French, who allegedly used the online handles such as “Orbit,” “@Orbit,” “@Orbit_g1rl,” “crysis,” “rootcrysis,” and “c0rps3,” was charged with conspiracy to commit computer fraud and abuse.The FBI has been working with a "confidential witness" to engage members of the NullCrew hacking group in a chat conversation on Skype, Twitter, and Cryptocat. Unknowingly, during the chat conversations, the NullCrew members discussed past, present, and future hacking attacks and shared current computer vulnerabilities used in the attacks.With the help of these information, the Federal officers tracked the IP address of one of the computers used in those five attacks as well as during other online attacks, which later found to be at French's address in Tennessee. All the records found from the victims’ computers show access from the same IP address at or around the time the attacks."Cyber crime sometimes involves new-age technology but age-old criminal activity ― unlawful intrusion, theft of confidential information, and financial harm to victims," said Zachary Fardon, who has appointed up-and-coming young Assistant U.S. Attorney for the Northern District of Illinois as a deputy section chief in charge of targeting Internet crime, in a statement."Hackers who think they can anonymously steal private business and personal information from computer systems should be aware that we are determined to find them, to prosecute pernicious online activity, and to protect cyber victims," Fardon added.If convicted, French faces a maximum sentence of 10 years in prison and a $250,000 fine. -
 The Supreme Court of India today struck down Section 66A of the Information Technology Act -- a controversial law that allowed law enforcement officials to arrest people for posting "offensive" comments on social networks and other internet sites.After hearing a clutch of petitions by defenders of free speech, the Supreme Court described the 2009 amendment to India's Information Technology Act known as section 66A as vague and ambiguous and beyond ambit of the constitutional right to freedom of speech."Section 66A is unconstitutional and we have no hesitation in striking it down," said Justice R F Nariman, reading out the judgement. "The public's right to know is directly affected by section 66A."SECTION 66A OF THE IT ACT
The Supreme Court of India today struck down Section 66A of the Information Technology Act -- a controversial law that allowed law enforcement officials to arrest people for posting "offensive" comments on social networks and other internet sites.After hearing a clutch of petitions by defenders of free speech, the Supreme Court described the 2009 amendment to India's Information Technology Act known as section 66A as vague and ambiguous and beyond ambit of the constitutional right to freedom of speech."Section 66A is unconstitutional and we have no hesitation in striking it down," said Justice R F Nariman, reading out the judgement. "The public's right to know is directly affected by section 66A."SECTION 66A OF THE IT ACT
The Information Technology Act 2000 was amended in the year 2008 and this amended act contains the 66A section. Under this section, "Any person who sends, by means of a computer resource or a communication device, —- any information that is grossly offensive or has menacing character; or
- any information which he knows to be false, but for the purpose of causing annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred or ill will, persistently by making use of such computer resource or a communication device,
- any electronic mail or electronic mail message for the purpose of causing annoyance or inconvenience or to deceive or to mislead the addressee or recipient about the origin of such messages,
shall be punishable with imprisonment for a term which may extend to three years and with fine."SECTION 66A MISUNDERSTOODBut, the legality of section 66A has been in Question from years. The Supreme Court earlier had said that terms like 'illegal', 'grossly offensive' and 'menacing character' were vague expressions and were likely to be dangerously twisted and misused.Section 66A act stops people to share and express their different or controversial opinion freely that may not necessarily be dangerous or a subject of 'grossly offensive' and 'menacing character'. Like for example, Theory of Evolution may be a ‘false information’ for those religious people who believes that God created the whole world, but it may be useful information for those who study Science.CASES IN WHICH SECTION 66A IS MISUSED BY POLITICIANSIn 2012, two young women – Shaheen Dhanda and Rinu Shrinivasan – were arrested in Palghar in Thane district, Mumbai under the Section 66A act for posting comments against the shutdown in Mumbai following Shiv Sena leader Bal Thackeray's death.The charges on two young ladies were later quashed by a Mumbai court, but this first case filled under Section 66A followed a number of arrests across the country for uploading political cartoons or posting comments on social network, which sparked outrage and fierce debate about online censorship in India.Some other controversial arrests under Section 66A of the IT act are as follows:- Recently, a class XII student was arrested for posting about Uttar Pradesh Minister Azam Khan on his Facebook timeline.
- Businessman Ravi Srinivasan was booked by police for allegedly tweeting that the son of then union minister P Chidambaram, Karti Chidambaram, was 'corrupt'.
- Last year, Devu Chodankar was arrested in Goa for writing on Goa+, a popular Facebook forum with over 47,000 members, that if elected to power, Modi would unleash a 'holocaust'.
- Ambikesh Mahapatra, a Jadavpur University professor, was arrested in Kolkata for forwarding a cartoon about Mamata Banerjee.
The government argued that the section 66A of the IT act was needed to protect the government data from hackers, to which the court was not at all impressed as this situation was already dealt with viruses and hacking for which Section 65 of the IT Act was relevant.-
 1
1
-
 An air-gapped computer system isolated from the Internet and other computers that are connected to external networks believes to be the most secure computers on the planet -- Yeah?? You need to think again before calling them 'safe'.A group of Israeli security researchers at the Cyber Security Labs from Ben Gurion University have found a new technique to hack ultra-secure air-gapped computers and retrieve data using only heat emissions and a computer’s built-in thermal sensors.WHAT IS AIR-GAPPED COMPUTERS ?Air-gapped computers or systems are considered to be the most secure and safest computer systems. These systems are isolated from the Internet or any other commuters that are connected to the Internet or external network.Air-gapped systems are used in situations that demand high security because it’s very difficult to siphon data from these systems, as it requires a physical access to the machine which is possible by using removable device such as a USB flash drive or a firewire cable.Air-gapped computers are classified military networks, the payment networks that process credit and debit card transactions for retailers, and in industrial control systems that operate critical infrastructure of the Nation. Even journalists use them to prevent intruders from remotely accessing sensitive data.HACKING AIR-GAPPED COMPUTERS USING HEATIn August 2014, security researchers from Ben Gurion University found a new way to breach an air-gapped system by using a method called Air-Hopper which utilizes little more than a mobile phone’s FM radio signals for data exfiltration.The same security researchers have now discovered a new technique, dubbed BitWhisper, that could be used by hackers to hack air-gapped computers by utilizing heat exchange between two computer systems.
An air-gapped computer system isolated from the Internet and other computers that are connected to external networks believes to be the most secure computers on the planet -- Yeah?? You need to think again before calling them 'safe'.A group of Israeli security researchers at the Cyber Security Labs from Ben Gurion University have found a new technique to hack ultra-secure air-gapped computers and retrieve data using only heat emissions and a computer’s built-in thermal sensors.WHAT IS AIR-GAPPED COMPUTERS ?Air-gapped computers or systems are considered to be the most secure and safest computer systems. These systems are isolated from the Internet or any other commuters that are connected to the Internet or external network.Air-gapped systems are used in situations that demand high security because it’s very difficult to siphon data from these systems, as it requires a physical access to the machine which is possible by using removable device such as a USB flash drive or a firewire cable.Air-gapped computers are classified military networks, the payment networks that process credit and debit card transactions for retailers, and in industrial control systems that operate critical infrastructure of the Nation. Even journalists use them to prevent intruders from remotely accessing sensitive data.HACKING AIR-GAPPED COMPUTERS USING HEATIn August 2014, security researchers from Ben Gurion University found a new way to breach an air-gapped system by using a method called Air-Hopper which utilizes little more than a mobile phone’s FM radio signals for data exfiltration.The same security researchers have now discovered a new technique, dubbed BitWhisper, that could be used by hackers to hack air-gapped computers by utilizing heat exchange between two computer systems.Dudu Mimran, the CTO of Cyber Security Labs, blogged on Monday, "BitWhisper is a demonstration for a covert bi-directional communication channel between two close by air-gapped computers communicating via heat. The method allows bridging the air-gap between the two physically adjacent and compromised computers using their heat emissions and built-in thermal sensors to communicate."
This new technique would allow hackers to stealthily siphon passwords or security keys from a secured system and send the sensitive data to an Internet-connected system which is placed in close proximity controlled by hackers.Hackers could also use their Internet-connected system to send malicious commands to the air-gapped computer using the same heat and sensor technique in order to cause more severe danger to the secured infrastructure.The team provided a video demonstration which shows how they were able to send a command from one computer to an adjacent air-gapped machine to re-position a toy missile launcher connected to the adjacent air-gapped system.HOW BITWHISPER WORKS ?Thermal sensors exist in computers used to trigger the internal fans to cool the PC down if overheating components such as CPU, GPU (graphics-processing unit) and other motherboard components threatens to damage them.BitWhisper utilizes these sensors to send commands to an air-gapped system or siphon data from it. The different heat patterns generated from the computer is regulated and binary data is modulated into thermal signals.The other adjacent PC in close proximity to the first one uses its built-in thermal sensors to measure the environmental changes. These changes are then sampled, processed, and demodulated into binary data in order to exfiltrate data.Experts demonstrated that the communication can also be bi-directional with both computers capable of transmitting or receiving commands and data by using the heat emitted by computers’ various components. A hacker simply needs to plant a piece of malware on each PC that need to communicate.The malware is designed to search for nearby systems by periodically emitting a thermal ping from the infected system in order to determine when a victim has placed his infected laptop next to a classified desktop system."Once a bridging attempt is successful, a logical link between the public network and the internal network in established," researchers explained. "At this stage, the attacker can communicate with the formerly isolated network, issuing commands and receiving responses."
Both the systems would then engage in a handshake, involving a sequence of "thermal pings", to establish a connection between them. But increased success of an operation is achieved outside work hours, when the internet-connected computer and the air-gapped one are in close proximity for an ongoing period and there is no need to conduct a handshake each time.FEW LIMITATIONS- The proof-of-concept attack requires both systems to first be compromised with malware.
- The attack currently allows for just 8 bits of data to be reliably transmitted over an hour, which is sufficient for an attacker to siphon a password or secret keys.
- The attack works only if the air-gapped system is within 40 centimeters/about 15 inches from the other computer controlled by an attacker.
However, researchers say they may be able to increase the distance between the two communicating computers and the speed of data transfer between them.FUTURE ATTACK MAY INVOLVE IoT DEVICESAccording to the security researchers, the future research might involve using the so-called internet of things (IoT) — an internet-connected heating and air conditioning system or a fax machine — as an attack vector instead of internet-connect computers.The team of researchers Mordechai Guri and Matan Munitz, under the guidance of Professor Yuval Elovici, planned to present their findings at a security conference in Tel Aviv next week and publish a paper on their research, "BitWhisper: Covert Signaling Channel between Air-Gapped Computers Using Thermal Manipulations."HOW BITWHISPER WORKS ?Thermal sensors exist in computers used to trigger the internal fans to cool the PC down if overheating components such as CPU, GPU (graphics-processing unit) and other motherboard components threatens to damage them.BitWhisper utilizes these sensors to send commands to an air-gapped system or siphon data from it. The different heat patterns generated from the computer is regulated and binary data is modulated into thermal signals.The other adjacent PC in close proximity to the first one uses its built-in thermal sensors to measure the environmental changes. These changes are then sampled, processed, and demodulated into binary data in order to exfiltrate data.Experts demonstrated that the communication can also be bi-directional with both computers capable of transmitting or receiving commands and data by using the heat emitted by computers’ various components. A hacker simply needs to plant a piece of malware on each PC that need to communicate.The malware is designed to search for nearby systems by periodically emitting a thermal ping from the infected system in order to determine when a victim has placed his infected laptop next to a classified desktop system."Once a bridging attempt is successful, a logical link between the public network and the internal network in established," researchers explained. "At this stage, the attacker can communicate with the formerly isolated network, issuing commands and receiving responses."
Both the systems would then engage in a handshake, involving a sequence of "thermal pings", to establish a connection between them. But increased success of an operation is achieved outside work hours, when the internet-connected computer and the air-gapped one are in close proximity for an ongoing period and there is no need to conduct a handshake each time.FEW LIMITATIONS- The proof-of-concept attack requires both systems to first be compromised with malware.
- The attack currently allows for just 8 bits of data to be reliably transmitted over an hour, which is sufficient for an attacker to siphon a password or secret keys.
- The attack works only if the air-gapped system is within 40 centimeters/about 15 inches from the other computer controlled by an attacker.
However, researchers say they may be able to increase the distance between the two communicating computers and the speed of data transfer between them.FUTURE ATTACK MAY INVOLVE IoT DEVICESAccording to the security researchers, the future research might involve using the so-called internet of things (IoT) — an internet-connected heating and air conditioning system or a fax machine — as an attack vector instead of internet-connect computers.The team of researchers Mordechai Guri and Matan Munitz, under the guidance of Professor Yuval Elovici, planned to present their findings at a security conference in Tel Aviv next week and publish a paper on their research, "BitWhisper: Covert Signaling Channel between Air-Gapped Computers Using Thermal Manipulations."-
 1
1
-

Security researcher has discovered some new features in the most dangerous Vawtrak, aka Neverquest, malware that allow it to send and receive data through encrypted favicons distributed over the secured Tor network
http://thehackernews.com/search/label/Tor%20network
The researcher, Jakub Kroustek from AVG anti-virus firm, has provided an in-depth analysis (PDFhttp://now.avg.com/wp-content/uploads/2015/03/avg_technologies_vawtrak_banking_trojan_report.pdf
) on the new and complex set of features of the malware which is considered to be one of the most dangerous threats in existence.
Vawtrak is a sophisticated piece of malwarehttp://thehackernews.com/search/label/Malware
in terms of supported features. It is capable of stealing financial information and executing transactions from the compromised computer remotely without leaving traces. The features include videos and screenshots capturing and launching man-in-the-middle attacks.
HOW VAWTRAK SPREADS ?
AVG anti-virus firm is warning users that it has discovered an ongoing campaign delivering Vawtrak to gain access to bank accounts visited by the victim and using the infamous Pony module in order to steal a wide range of victims’ login credentials.
The Vawtrak Banking Trojan spreads by using one of the three ways:- Drive-by download – spam email attachments or links to compromised sites
- Malware downloader – like Zemot or Chaintor
- Exploit kit – like as Angler Exploit Kit
According to the researcher, Vawtrak is using the Tor2Web proxy to receive updates from its developers.
"Of particular interest from a security standpoint is that by using Tor2web proxy, it can access update servers that are hosted on the Tor hidden web services without installing specialist software such as Torbrowser," Kroustek says. "Moreover, the communication with the remote server is done over SSL, which adds further encryption."
The latest Vawtrak sample uses steganography to hide update files within favicons in order to conceal the malicious downloads. Favicons are the small images used by the websites to add icon to website bookmarks and browser tabs.
Once executed in the victim’s machine, Vawtrak performs the following actions:- Disables antivirus protection.
- Inject custom code in a user-displayed web pages (this is mostly related to online banking)
- Steals passwords, digital certificates, browser history, and cookies.
- Surveillance of the victim (key logging, taking screenshots, capturing video)
- Creates a remote access to a user’s machine (VNC, SOCKS)
- Automatic updating.
AFFECTED COUNTRIES
Based on their statistics, Vawktrak is infecting banking, gaming and social network users mainly across the countries including United Kingdom, the United States, and Germany. Although, users in Australia, New Zealand, and across Europe are also affected.
AVG concluded following their analysis of the malware that "Vawtrak is like a Swiss Army knife for its operators because of its wide range of applications and available features." CP Moderator Message: Mr Grumpy - Coded links
CP Moderator Message: Mr Grumpy - Coded links
-
I get to drive it next Right ?
Cool ride Bro !
-
 1
1
-
-
http://boombeachhacktool.com/


here is another one my friend
http://www.boombeachhacktool.org/
-
 2
2
-
-
 China finally admits it has special cyber warfare units — and a lot of them.From years China has been suspected by U.S. and many other countries for carrying out several high-profile cyber attacks, but every time the country strongly denied the claims. However, for the first time the country has admitted that it does have cyber warfare divisions – several of them, in fact.In the latest updated edition of a PLA publication called The Science of Military Strategy, China finally broke its silence and openly talked about its digital spying
China finally admits it has special cyber warfare units — and a lot of them.From years China has been suspected by U.S. and many other countries for carrying out several high-profile cyber attacks, but every time the country strongly denied the claims. However, for the first time the country has admitted that it does have cyber warfare divisions – several of them, in fact.In the latest updated edition of a PLA publication called The Science of Military Strategy, China finally broke its silence and openly talked about its digital spyinghttp://thehackernews.com/search/label/surveillance
and network attack capabilities and clearly stated that it has specialized units devoted to wage war on computer networks.An expert on Chinese military strategy at the Center for Intelligence Research and Analysis, Joe McReynolds toldhttp://www.thedailybeast.com/articles/2015/03/18/china-reveals-its-cyber-war-secrets.html
TDB that this is the first time when China has explicit acknowledged that it has secretive cyber-warfare units, on both the military as well as civilian-government sides.
CHINESE CYBER WARFARE UNITSAccording to McReynolds, China has three types of operational military units:- Specialized military forces to fight the network -- The unit designed to carry out defensive and offensive network attacks.
- Groups of experts from civil society organizations -- The unit has number of specialists from civilian organizations – including the Ministry of State Security (its like China’s CIA), and the Ministry of Public Security (its like FBI) – who are authorized to conduct military leadership network operations.
- External entities -- The unit sounds a lot like hacking-for-hire mercenaries and contains non-government entities (state-sponsored hackers) that can be organized and mobilized for network warfare operations.
According to experts, all the above units are utilized in civil cyber operations, including industrial espionage against US private companies to steal their secrets."It means that the Chinese have discarded their fig leaf of quasi-plausible deniability," McReynolds said. "As recently as 2013, official PLA [People's Liberation Army] publications have issued blanket denials such as, 'The Chinese military has never supported any hacker attack or hacking activities.' They can't make that claim anymore."CHINESE CYBER UNIT 61398
In 2013, American private security firm Mandiant published a 60-page report that detailed about the notorious Chinese hacking group 'Unit 61398http://thehackernews.com/2013/02/mandiant-revealed-chinese-apt1-cyber.html
', suspected of waging cyber warfare against American companies, organizations and government agencies from or near a 12-story building on the outskirts of Shanghai.The UNIT 61398 also targeted a number of government agencies and companies whose databases contain vast and detailed information about critical United States infrastructure, including pipelines, transmission lines and power generation facilities.
MOST WANTED CHINESE HACKERS
Last year, the United States filed criminal chargeshttp://thehackernews.com/2014/05/us-charges-five-chinese-military.html
against five Chinese military officials, named Wang Dong, Sun Kailiang, Wen Xinyu, Huang Zhenyu, and Gu Chunhui, for hacking and conducting cyber espionage against several American companies.
The alleged hackers were said to have worked with the PLA’s Unit 61398 in Shanghai. Among spying on U.S companies and stealing trade secrets, they had also accused for stealing information about a nuclear power plant design and a solar panel company’s cost and pricing data.Subscribe Our Newsletter CP Moderator Message: Mr Grumpy - Coded links
CP Moderator Message: Mr Grumpy - Coded links
-
 1
1
-
 The Annual Pwn2Own Hacking Competition 2015 held in Vancouver is over and participants from all over the world nabbed $557,500 in bug bounties for 21 critical bugs in top four web browsers as well as Windows OS, Adobe Reader and Adobe Flash.During the second and final day of this year’s hacking contest, the latest version of all the four major browsers including Microsoft Internet Explorer, Mozilla Firefox, Google Chrome, and Apple Safari, were compromised by the two security researchers.Sponsored by HP's Zero Day Initiative program, the Pwn2Own Hacking Competition ran two days at a security conference in Vancouver, Canada. The final highlights for Pwn2Own 2015 are quite impressive:
The Annual Pwn2Own Hacking Competition 2015 held in Vancouver is over and participants from all over the world nabbed $557,500 in bug bounties for 21 critical bugs in top four web browsers as well as Windows OS, Adobe Reader and Adobe Flash.During the second and final day of this year’s hacking contest, the latest version of all the four major browsers including Microsoft Internet Explorer, Mozilla Firefox, Google Chrome, and Apple Safari, were compromised by the two security researchers.Sponsored by HP's Zero Day Initiative program, the Pwn2Own Hacking Competition ran two days at a security conference in Vancouver, Canada. The final highlights for Pwn2Own 2015 are quite impressive:- 5 bugs in the Windows operating system
- 4 bugs in Internet Explorer 11
- 3 bugs in Mozilla Firefox
- 3 bugs in Adobe Reader
- 3 bugs in Adobe Flash
- 2 bugs in Apple Safari
- 1 bug in Google Chrome
- $557,500 USD bounty paid out to researchers
The star of the show was South Korean security researcher Jung Hoon Lee, nicknamed "lokihardt," who worked alone and nabbed the single highest payout of the competition in the Pwn2Own history, an amazing bounty of $110,000 in just two minutes.Lee was able to take down both stable and beta versions of Google Chrome browser by exploiting a buffer overflow race condition bug in the browser and nabbed $75,000 as bug bounty.For this same bug, Lee also nabbed an extra $25,000 for gaining system access by targeting an information leak and a race condition in two Windows kernel drivers. To hack the beta version of Chrome, Google’s Project Zero rewarded Lee by an extra $10,000. So, he earned a grand total of $110,000."To put it another way, lokihardt earned roughly $916 a second for his two-minute demonstration," HP's security research team wrote in a blog posthttp://h30499.www3.hp.com/t5/HP-Security-Research-Blog/Pwn2Own-2015-Day-Two-results/ba-p/6722884#.VRmBniipxIn
Earlier in the day, Lee also earned $65,000 for hacking the 64-bit Internet Explorer 11 with a time-of-check to time-of-use (TOCTOU) vulnerability that gained him read/write privileges on the browser. He used a sandbox escape via JavaScript injection to evade Windows defenses mechanism.Thursday. "There are times when 'Wow' just isn't enough."By using a use-after-free exploit and a separate sandbox escape, Lee also took down Apple's Safari browser. The hack earned him $50,000 and brought his total winnings to $225,000 from the contest.CyberPhoenix Rockz Best ! CP Moderator Message: Mr Grumpy - Coded links
CP Moderator Message: Mr Grumpy - Coded links
-
 1
1
-
 After the latest Microsoft Patch Tuesday updates that came with important patches for Stuxnet and FREAK encryption-downgrade attack, now its time to update your Adobe Flash Player.Adobe has rolled-out an update for its popular Flash Player software that patches a set of 11 critical security vulnerabilities in its program, most of which potentially allow hackers to remotely execute arbitrary code on vulnerable systems.AFFECTED SOFTWAREAll versions prior to the latest version 17.0.0.134 of the Flash Player are affected on Windows and Mac OS X machines. Therefore, Adobe Flash Player installed with Google Chrome, as well as Internet Explorer 10 and 11 on Windows 8 and Windows 8.1, should automatically update to the newest version 17.0.0.134.In addition, Adobe Flash Player 11.2.202.442 for Linux and Flash Player Extended Support Release 13.0.0.269 for Windows and Mac OS X are also affected by the vulnerabilities.
After the latest Microsoft Patch Tuesday updates that came with important patches for Stuxnet and FREAK encryption-downgrade attack, now its time to update your Adobe Flash Player.Adobe has rolled-out an update for its popular Flash Player software that patches a set of 11 critical security vulnerabilities in its program, most of which potentially allow hackers to remotely execute arbitrary code on vulnerable systems.AFFECTED SOFTWAREAll versions prior to the latest version 17.0.0.134 of the Flash Player are affected on Windows and Mac OS X machines. Therefore, Adobe Flash Player installed with Google Chrome, as well as Internet Explorer 10 and 11 on Windows 8 and Windows 8.1, should automatically update to the newest version 17.0.0.134.In addition, Adobe Flash Player 11.2.202.442 for Linux and Flash Player Extended Support Release 13.0.0.269 for Windows and Mac OS X are also affected by the vulnerabilities.
So, users of Flash Player on Linux should update to version 11.2.202.451 and Flash Player Extended Support Release on Windows and Mac are recommended to update to version 13.0.0.277.REMOTE CODE EXECUTIONTotal 9 Remote Code Execution vulnerabilities patches are included in the latest Adobe Flash PLayer update. An attacker could serve a specially crafted Flash file to trigger the vulnerabilities, which would lead to the execution of attacker's code in order to take control of a target system.Most of the vulnerabilities in Adobe Flash Player have been reported by security researchers from Google’s Project Zero team. Other security companies that disclosed the vulnerabilities are Hewlett-Packard, NCC Group, Intel and McAfee.LIST OF VULNERABILITIESThe list of all the patched vulnerabilities along with their impacts is given below:- CVE-2014-0332 — Remote code execution via memory corruption vulnerability.
- CVE-2015-0333 — Remote code execution via memory corruption vulnerability.
- CVE-2015-0334 — Remote code execution from type confusion vulnerability.
- CVE-2015-0335 — Remote code execution via memory corruption vulnerability.
- CVE-2015-0336 — Remote code execution from type confusion vulnerability.
- CVE-2015-0337 — A 'cross domain policy bypass' flaw.
- CVE-2015-0338 — Remote code execution from integer overflow vulnerability.
- CVE-2015-0339 — Remote code execution via memory corruption vulnerability.
- CVE-2015-0340 — A 'File upload restriction bypass' flaw.
- CVE-2015-0341 — Remote code execution from a 'use-after-free' vulnerability.
- CVE-2015-0342 — Remote code execution from a 'use-after-free' vulnerability.
According to Adobe, none of the vulnerabilities are being publicly exploited in the wild thus far. However, we all know that immediately after the the release of updated versions, hackers starts exploiting these critical flaws in order to catch out people who haven't updated their machines.Therefore users and administrators running Adobe Flash Player on Windows, Mac OS X and Linux are advised to update their software to the most recent version of the software in an attempt to protect their systems from cyber attacks.-
 1
1
-
 Are you aware of everything that your users are accessing from your environment?While most of the time, non-work-related Internet browsing is harmless (looking at pictures of cats, online shopping, social media, etc.) there are some instances where you could be an unknowing and unwilling participant in criminal activity. That is, when users hide that activity via the Tor network, or the Dark Net.The Onion Router, better known as "Tor", an open source project, launched in 2002, is designed to allow a user to browse the Internet anonymously via a volunteer network of more than 5000 relays. It doesn't share your identifying information like your IP address and physical location with websites or service providers.A user that navigate Internet using Tor, it's quite difficult to trace its activities ensuring his online privacy. There are arguably legitimate uses for this technology, such as providing Internet access in repressively regulated countries.Tor has been a favorite target of intelligence agencies. NSA targeted the Tor users, using a zero-day vulnerability in Firefoxbrowser, bundled with Tor, that allowed them to get the real IP address of the anonymous Tor users.Using same techniques, FBI was also able to track the Owner of 'Freedom Hosting', the biggest service provider for sites on the encrypted Tor network, hosted many child pornography sites.
Are you aware of everything that your users are accessing from your environment?While most of the time, non-work-related Internet browsing is harmless (looking at pictures of cats, online shopping, social media, etc.) there are some instances where you could be an unknowing and unwilling participant in criminal activity. That is, when users hide that activity via the Tor network, or the Dark Net.The Onion Router, better known as "Tor", an open source project, launched in 2002, is designed to allow a user to browse the Internet anonymously via a volunteer network of more than 5000 relays. It doesn't share your identifying information like your IP address and physical location with websites or service providers.A user that navigate Internet using Tor, it's quite difficult to trace its activities ensuring his online privacy. There are arguably legitimate uses for this technology, such as providing Internet access in repressively regulated countries.Tor has been a favorite target of intelligence agencies. NSA targeted the Tor users, using a zero-day vulnerability in Firefoxbrowser, bundled with Tor, that allowed them to get the real IP address of the anonymous Tor users.Using same techniques, FBI was also able to track the Owner of 'Freedom Hosting', the biggest service provider for sites on the encrypted Tor network, hosted many child pornography sites.
However, Mozilla has then fixed that Firefox flaw exploited by government law enforcement officials.Moreover, Tor is often associated with illicit activity (child pornography, selling controlled substances, identity theft, money laundering, and so on). Most admins will want to prohibit their users from using the Tor network due to its association with nefarious activity.Since the point of origin is nearly impossible to determine with conventional means, many bad actors leverage the Tor network to hide the location of Command & Control servers, machines taking ransomware payments, etc. This makes identifying these them and their malware that much harder.Users browsing the Tor network (for illicit purposes or not) from your environment can open you up to hosting malicious/illegal content, Ransomware infection, or unknowingly participating in other malicious activity. Therefore it is also known as DeepNet or Deep Web.
To know more detail about the Deep Web you can read our detailed article, "What is the Deep Web? A first trip into the abyss".WHAT I CAN DO ABOUT TOR?AlienVault Unified Security ManagementTM (USM) can help. USM provides asset discovery, vulnerability assessment, threat detection (IDS), behavioral monitoring and SIEM in a single console, plus weekly threat intelligence updates developed by the AlienVault Labs threat research team.The correlation directives and IDS signatures in AlienVault Unified Security Management (USM) can detect when a system is attempting to resolve a Tor domain, and allow you to take corrective action. Plus, new & updated correlation directives developed by the experts at AlienVault Labs are pushed to USM weekly, enabling detection of emerging threats.Learn more about AlienVault USM:- Download a free 30-day trial
- Watch a demo on-demand
- Play with USM in our product sandbox (no download required)
-
 1
1
-
Welcome Guy's hope this helps
Thankz 4 the reading !
-
Even though Avast is one of my favorite antivirus products, there have been times when I've needed to uninstall or remove it. Corrupted virus signatures have caused it not to update properly, or it wont start properly and it needs to be reinstalled. Maybe corrupted files are causing 100% CPU usage. These and other issues can cause you to uninstall and reinstall your antivirus product.
Whatever the reason for needing to uninstall Avast, I've listed the best procedure for doing this below:
Normal Uninstall
The first thing you want to try is to locate Avast in the Add/Remove Control Panel and try to remove it from there. Follow these instructions to accomplish this.
1) Click on Start, Control Panel
2) Open Add/Remove Programs
3) Find Avast in the Programs list and highlight it
4) Click Remove and follow the prompts to uninstall Avast
Using the Avast Uninstall Utility
If for some reason the normal uninstall does not work, you may have to download Avast's own Uninstall Utility.
1) Click on the following link and download the Avast Uninstall Utility to your desktop
http://files.avast.com/files/eng/aswclear.exe
2) Double-click on the file ASWCLEAR and run it
3) You should see the following screen

4) Click on the ellipsis and choose the folder where Avast is installed. This folder is usually in the Program Files directory. Ex. C:\Program Files\Avast
Be very careful which folder you choose since whatever folder is chosen will be completely deleted from your computer.
5) Once the uninstall has completed, reboot your computer. You may then try to reinstall it or another antivirus.
If for some reason the uninstall utility does not remove it, you may have to reinstall a newer version of Avast to then proceed to uninstall or you may have an issue where
multiple antivirus programs are showing in the Windows Security Center.
 CP Moderator Message: Mr Grumpy - Coded links
CP Moderator Message: Mr Grumpy - Coded links
-
 3
3
-
-


http://linuxfreedom.com/
-
 1
1
-
-
Microsoft has come up with its most important Patch Tuesday for this year, addressing the recently disclosed critical the FREAK encryption-downgrade attack, and a separate five-year-old vulnerability leveraged by infamous Stuxnet malware to infect Windows operating system.Stuxnet malware, a sophisticated cyber-espionage malware allegedly developed by the US Intelligence and Israeli government together, was specially designed to sabotage the Iranian nuclear facilities a few years ago. First uncovered in 2010, Stuxnet targeted computers by exploiting vulnerabilities in Windows systems.Thankfully, Microsoft has issued a patch to protect its Windows machines that have been left vulnerable to Stuxnet and other similar attacks for the past five years. The fixes are included in MS15-020 which resolves Stuxnet issue.The company has also issued an update that patches the FREAK encryption vulnerability in its SSL/TSL implementation called Secure Channel (Schannel). The fixes for the vulnerability are included in MS15-031.As we have mentioned in our previous report, FREAK — short for Factoring attack on RSA-EXPORT Keys — was initially thought to be associated with Apple's Safari and Android's stock browsers, but it was found to affect Windows PCs as well.This decades-old FREAK vulnerability allows an attacker on your network to force the software using Schannel component such as Internet Explorer to use weak encryption over the web, so that they can easily decrypt the intercepted HTTPS connections.Among these two critical issues, the company has also released a bunch of other updates. Microsoft's March 2015 Patch Tuesday update bundles a total of 14 security-related updates for 43 vulnerabilities affecting Internet Explorer, VBscript, Text Services, Adobe Font Drivers, and Office.- MS15-018 - A Cumulative Security Update, rated as 'critical', affects all supported versions of Internet Explorer and addresses a number of Memory Corruption vulnerabilities, two elevation of privilege vulnerabilities, and a VBscript memory corruption vulnerability.
- MS15-019 - This update addresses a scripting vulnerability in some older versions of Windows operating systems. The vulnerability doesn't affect Windows 7 and later desktop versions.
- MS15-021 - It addresses eight vulnerabilities in the Adobe Font Driver components for Windows and Windows Server exploitable through a malicious website or file. It is also rated 'critical' due to the possibility of remote code execution.
- MS15-022 - This update fixes three unknown flaws in Office document formats as well as multiple cross-site scripting (XSS) issues for SharePoint Server, and applies to all supported versions of Microsoft Office, as well as the server-based Office Web Apps and SharePoint Server products.
- MS15-023 - This bulletin, rated as 'important', addresses four vulnerabilities in the Windows Kernel-Mode driver allowing elevation of privilege and information disclosure attacks by launching a specially-crafted application.
Rest of all, MS15-024, MS15-025, MS15-027, MS15-028, MS15-29 and MS15-30, are rated as 'important' and affected Windows and Windows Server. Microsoft is advising all its users and administrators to install the new updates as soon as possible.-
 1
1
-

ImgBurn is a lightweight CD / DVD / HD DVD / Blu-ray burning application that everyone should have in their toolkit!
It has several 'Modes', each one for performing a different task:
- Read - Read a disc to an image file
- Build - Create an image file from files on your computer or network - or you can write the files directly to a disc
- Write - Write an image file to a disc
- Verify - Check a disc is 100% readable. Optionally, you can also have ImgBurn compare it against a given image file to ensure the actual data is correct
- Discovery - Put your drive / media to the test! Used in combination with DVDInfoPro, you can check the quality of the burns your drive is producing
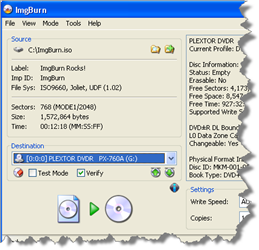
ImgBurn supports a wide range of image file formats - including BIN, CCD, CDI, CUE, DI, DVD, GI, IMG, ISO, MDS, NRG and PDI.
It can burn Audio CD's from any file type supported via DirectShow / ACM - including AAC, APE, FLAC, M4A, MP3, MP4, MPC, OGG, PCM, WAV, WMA and WV.
You can use it to build DVD Video discs (from a VIDEO_TS folder), HD DVD Video discs (from a HVDVD_TS folder) and Blu-ray Video discs (from a BDAV / BDMV folder) with ease.
It supports Unicode folder/file names, so you shouldn't run in to any problems if you're using an international character set.
ImgBurn supports all the Microsoft Windows OS's - Windows 95, Windows 98, Windows Me, Windows NT4, Windows 2000, Windows XP, Windows 2003, Windows Vista, Windows 2008, Windows 7 and Windows 8 (including all the 64-bit versions). If you use Wine, it should also run on Linux and other x86-based Unixes.
It's a very flexible application with several advanced features that are often lacking in other tools, especially when it comes to burning DVD Video discs. It supports all the latest drives without the need for updates (including booktype / bitsetting / advanced settings on many of the major ones - i.e. BenQ, LiteOn, LG, NEC, Optiarc, Pioneer, Plextor, Samsung, Sony).
There is an image queue system for when you're burning several images (which you can automatically share between multiple drives if you have more than one) and an easy-to-use layer break selection screen for double layer DVD Video jobs. The Automatic Write Speed feature allows you store your favourite burn speed settings on a per 'Media ID' basis, right down to a drive by drive level. Data captured during the burn (write speed, buffer levels etc) can be displayed / analysed using DVDInfoPro.
Whilst ImgBurn is designed to work perfectly straight out of the box, advanced users will appreciate just how configurable it is.
Oh and let's not forget the best thing about it.... it's 100% FREE ;-)
Please do not use this software to make illegal copies of copyrighted discs.
Download here
http://imgburn.com/
-
 1
1
-
this site has heart warming stories plus much much more you will find yourself hooked
http://www.elitereaders.com/
-
 1
1
-



Bitdefender Adware Removal Tool for PC (DDL = Direct download link)
in Link Heaven
Posted · Report reply
Thankz 4 This Bro !